How CDN Protection Defends Against DDoS and CC Attacks?
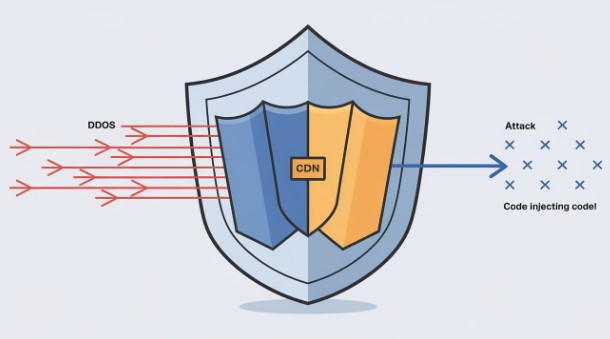
Introduction to CDN Protection Against Cyber Attacks
In today’s digital landscape, Hong Kong hosting providers face increasing threats from DDoS and CC attacks. Content Delivery Network (CDN) protection has emerged as a crucial defense mechanism for maintaining server security and performance. This technical guide explores how Content Delivery Network defense effectively mitigates these attacks while ensuring optimal service delivery.
Understanding DDoS and CC Attacks
DDoS (Distributed Denial of Service) attacks overwhelm servers by flooding them with massive traffic from multiple sources. CC (Challenge Collapsar) attacks, a subset of Layer 7 DDoS attacks, specifically target web application resources through seemingly legitimate HTTP requests. Here’s a typical DDoS attack pattern analysis:
# Python code example for basic DDoS detection
def detect_ddos(requests_log, threshold=1000):
ip_counts = {}
timeframe = 60 # seconds
for request in requests_log:
ip = request['ip']
timestamp = request['timestamp']
# Count requests per IP within timeframe
if ip in ip_counts:
ip_counts[ip] += 1
else:
ip_counts[ip] = 1
if ip_counts[ip] > threshold:
return True # Potential DDoS detected
return False
CDN Defense Mechanisms
Content Delivery Network defense works through a distributed network of servers that provide multiple layers of defense:
- Traffic Distribution: Spreads attack traffic across multiple points of presence (PoPs)
- Anycast Network: Routes requests to the nearest available server
- Traffic Scrubbing: Filters malicious traffic before reaching origin servers
Technical Implementation of CDN Protection
Here’s a typical Content Delivery Network configuration for DDoS defense:
# Example CDN configuration in nginx
http {
# Rate limiting
limit_req_zone $binary_remote_addr zone=one:10m rate=1r/s;
# Custom rules for CC attack prevention
if ($http_user_agent ~* (curl|wget|python)) {
return 403;
}
# Enable WAF rules
modsecurity on;
modsecurity_rules_file /etc/nginx/modsecurity/main.conf;
}
Advanced Protection Features
Modern CDN defense includes sophisticated features:
- AI-based threat detection
- SSL/TLS protection
- Real-time traffic analysis
- Custom rule creation
Best Practices for Hong Kong Servers
For optimal defense of Hong Kong hosting services:
- Deploy multiple PoPs across APAC region
- Implement proper SSL termination
- Regular security audits
- 24/7 monitoring systems
Implementation Guide
Step-by-step process for implementing CDN protection:
# Example implementation steps
1. DNS Configuration
- Update A records
- Configure CNAME
- Set TTL values
2. SSL Setup
- Generate CSR
- Install certificates
- Enable HTTPS
3. Rule Configuration
- Set rate limiting
- Configure WAF rules
- Define custom rules
Future Trends in CDN Protection
The evolution of CDN protection continues with emerging technologies like edge computing, AI-driven threat detection, and quantum-resistant encryption. These advancements will further enhance the security capabilities of Hong Kong hosting providers against sophisticated cyber attacks.
Conclusion
CDN protection serves as a critical component in defending against DDoS and CC attacks for Hong Kong hosting services. By implementing proper CDN security measures, organizations can ensure robust defense while maintaining optimal performance and availability.

